Our evolution is rooted in hunting. For millennia, it served as an essential survival skill for our ancestors — one that advanced with time, surroundings, and resources available. Today, hunting is no longer limited to pursuing and capturing wild animals and birds. It has now extended to the digital forest, where new adversaries operate within the intricate web of cyberspace.
As we embrace this digital landscape, enterprises worldwide are pressed to deal with these threats proactively. Why? To retain their credibility, meet customer expectations, and reduce downtime losses — the average cost of a cyberattack is $4.45 million. In this situation, proactive safety measures like threat hunting are vital for businesses.
Threat hunting in a digital forest
Threat hunting shares certain similarities with traditional hunting. In both cases, you need to clearly understand the landscape and the threats you need to neutralize.
However, cybersecurity threat hunting begins with a threat hypothesis based on the intelligence gathered. It can be an educated guess about a potential cyber attack or malicious activity within your network. You can collect threat intelligence by monitoring data logs from XDR, SIEM, and security analytics tools.
Once you zero down on the hypothesis, the execution phase dives into the nitty-gritty. Threat hunters use chosen techniques to collect data from various sources and meticulously analyze it for anomalies or signs that align with the hypothesis. If any suspicious activity is found, they’ll deep dive with forensics tools, isolate systems whenever needed, and meticulously follow the breadcrumbs to uncover the entire scope of the potential threat. Throughout this process, everything is documented to improve future hunts, share knowledge, and provide a clear picture for the reporting phase. Effective threat hunting reduces the time between intrusion and discovery — shortening the damage done.
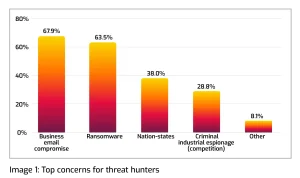
Roadblocks to effective threat hunting
Given the sophisticated nature of threat hunting, there are some obvious challenges. One prevalent challenge in cybersecurity is knowing where to hunt for threats, as digital indicators of compromise are usually hidden and scattered.
Some common challenges include:
- Data overload and false positives: Many security teams need help staying current with the exponentially growing data deluge – with threat hunters reporting spending significant time chasing down false positives. Finding real threats amid these volumes of data is even more complex than finding a needle in the haystack.
- Lack of skilled personnel and resources: Threat hunting is a highly specialized skill, and the need for qualified professionals is a pressing concern. This scarcity can pose significant challenges for organizations in establishing and sustaining effective threat-hunting programs.
- Evolving threats and attacker tactics: Cybercriminals constantly develop new techniques to evade detection. Threat hunters must stay current on the latest threats and adapt their tactics accordingly.
- AI adoption is a double-edged sword: Even though AI can automate some threat-hunting tasks and improve threat detection, it has risks. Attackers can mislead AI models, and organizations must evaluate these risks carefully before deploying them.
Key considerations
Threat hunting is a talent and virtue that needs to be cultivated. Enterprises need to focus their efforts on the number of available staff and their skill level. They can start their journey by building dedicated training modules and training future generations of threat hunters. This will help enterprises bridge the growing skill gap.
Here are why you should focus on the human element of threat hunting and constantly upskill your team:
- When it comes to cyber threats, your unique human expertise is indispensable. Humans can understand the modus operandi of attackers, which allows them to comprehend threat intelligence and uncover patterns that may elude mere software solutions. The human role is not just important; it’s irreplaceable.
- Tools like SIEM, XDR, and others can only create the foundation you need for threat hunting, but they don’t have the context to understand the data. Human analysts, on the other hand, come with a subjective and objective understanding of your IT infrastructure and industry. This gives them added context to categorize a threat.
- One of the primary concerns around automated systems is their inability to adapt. While the threats keep evolving, automation rules fail to keep up with these changes. Adding a human element of creative and adaptable thinking can help solve this knot.
Towards a collaborative future
As you build an internal team of threat hunters, collaborating with managed security service providers can be a strategic move. You can leverage their expert threat hunters to manage your IT environment and stay safe from emerging cyber threats. Your managed cybersecurity partners can even train your team and make the transition more seamless.
Many businesses are already making significant investments in both human and technological resources. As the threat landscape changes, so does the understanding of the need for more sophisticated threat-hunting capabilities, from AI integration to better data management and staff knowledge. Without a doubt, these notions will influence cybersecurity defense measures well into the future.
If you’re looking to augment your cybersecurity team with seasoned threat hunters, you can reach out to discuss how HTC Global Services can help you protect your IT assets and sensitive data.





